Trojan in network security cheap
Trojan in network security cheap, Trojan Horse Meaning Examples Prevention cheap
$70.00
SAVE 50% OFF
$35.00
$0 today, followed by 3 monthly payments of $11.67, interest free. Read More
Trojan in network security cheap
Trojan Horse Meaning Examples Prevention
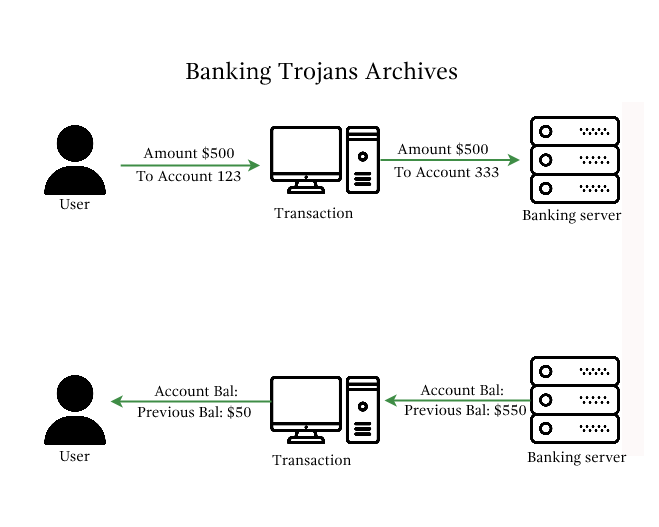
What are Banking Trojans GeeksforGeeks
What are Trojan Viruses and How Do These Threats Work Top Cloud
Trojan Horse Meaning Examples Prevention
Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus
What is Trojan Horse Virus Protect Yourself Against Trojan Viruses
Description
Product code: Trojan in network security cheap
What is a Trojan Virus Trojan Horse Malware Imperva cheap, How trojan malware is evolving to survive and evade cybersecurity cheap, Trojan Horse Meaning Examples Prevention cheap, What are Banking Trojans GeeksforGeeks cheap, What are Trojan Viruses and How Do These Threats Work Top Cloud cheap, Trojan Horse Meaning Examples Prevention cheap, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus cheap, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses cheap, What is Proxy Trojan GeeksforGeeks cheap, What is a Trojan Horse U.S. News cheap, How to prevent a Remote Access Trojan or RAT The Security Buddy cheap, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet cheap, Hardware Trojan GeeksforGeeks cheap, Trojan Horse CyberHoot Cyber Library cheap, What s the Difference Between Malware Trojan Virus and Worm cheap, CCNA Security Worm Virus and Trojan Horse Attacks cheap, What are Trojans in Cybersecurity Concept Examples Types and cheap, What is a Trojan Horse Virus Types and How to Remove it cheap, Trojan horse virus mal ware cyber security attack Vector Image cheap, What is Trojan Horse Trojan Virus Cyber Security Tutorial 14 cheap, Trojans What s the real deal Malwarebytes Labs cheap, What Is Trojan Trojan Horse Virus In Cybersecurity Trojan in cheap, Trojan horse Network security Computer network Malware Bank cheap, Unit 7 Organisational Systems Security task 1 Computer cheap, Using deep learning to detect digitally encoded DNA trigger for cheap, Group IB discovers banking Trojan malware targeting users of cheap, Trojan virus backdoors PPT cheap, Cyber Security Terms Everyone Should Know ThriveDX cheap, Worm vs Virus vs Trojan The Security Buddy cheap, a A hardware Trojan circuit leaking confidential information and cheap, Malware repo 1 Backdoor Trojan System cheap, Trojan Horse Computer security Computer program Network security cheap, What Is a Trojan Horse Arctic Wolf cheap, What Is A Trojan Attack Understanding The Invisible Threat cheap, How to Detect and Remove Computer Trojan Horse Viruses cheap.
What is a Trojan Virus Trojan Horse Malware Imperva cheap, How trojan malware is evolving to survive and evade cybersecurity cheap, Trojan Horse Meaning Examples Prevention cheap, What are Banking Trojans GeeksforGeeks cheap, What are Trojan Viruses and How Do These Threats Work Top Cloud cheap, Trojan Horse Meaning Examples Prevention cheap, Trojan Horse Virus Trojan Horse Malware What is a Trojan Virus cheap, What is Trojan Horse Virus Protect Yourself Against Trojan Viruses cheap, What is Proxy Trojan GeeksforGeeks cheap, What is a Trojan Horse U.S. News cheap, How to prevent a Remote Access Trojan or RAT The Security Buddy cheap, What Is a Trojan Horse Trojan Virus and Malware Explained Fortinet cheap, Hardware Trojan GeeksforGeeks cheap, Trojan Horse CyberHoot Cyber Library cheap, What s the Difference Between Malware Trojan Virus and Worm cheap, CCNA Security Worm Virus and Trojan Horse Attacks cheap, What are Trojans in Cybersecurity Concept Examples Types and cheap, What is a Trojan Horse Virus Types and How to Remove it cheap, Trojan horse virus mal ware cyber security attack Vector Image cheap, What is Trojan Horse Trojan Virus Cyber Security Tutorial 14 cheap, Trojans What s the real deal Malwarebytes Labs cheap, What Is Trojan Trojan Horse Virus In Cybersecurity Trojan in cheap, Trojan horse Network security Computer network Malware Bank cheap, Unit 7 Organisational Systems Security task 1 Computer cheap, Using deep learning to detect digitally encoded DNA trigger for cheap, Group IB discovers banking Trojan malware targeting users of cheap, Trojan virus backdoors PPT cheap, Cyber Security Terms Everyone Should Know ThriveDX cheap, Worm vs Virus vs Trojan The Security Buddy cheap, a A hardware Trojan circuit leaking confidential information and cheap, Malware repo 1 Backdoor Trojan System cheap, Trojan Horse Computer security Computer program Network security cheap, What Is a Trojan Horse Arctic Wolf cheap, What Is A Trojan Attack Understanding The Invisible Threat cheap, How to Detect and Remove Computer Trojan Horse Viruses cheap.